👋 Introduction
SelfPrivacy - mobile app deploys a server with ready-to-use services:
- Password manager
- Messenger
- VPN
- File storage
- Conferences
- ... and many other services
⚠️ Beta
The current release is not yet ready for everyday use by an unskilled user.
🔋Motivation
Every internet user is forced to use centralized services sacrificing privacy and personal freedoms:
- Accepts incomprehensible licenses
- Endures ads
- Gives his data to unknown person
- End up in a "[recommendation bubble] (https://ru.wikipedia.org/wiki/Пузырь_фильтров)".
- Subject to censorship, blocking
We don't want it that way. We want digital independence and privacy.md of our data.
Our mission is to offer an alternative. Your services - your rules:
- No license agreements, advertising, surveillance, telemetry, bans and censorship
- Your data is stored on your server and belongs only to you
🧑💻 About us
International team of independent professionals:
- Zholnay Kirill - Founder/CEO/CISO. For more than 15 years builds and protects corporate infrastructure in medium and large companies
- ilchub - core-team DevOps, Backend-dev
- kherel - core-team Flutter dev
- nikolai - QA Engeneer
- and a lot of cool cotributors and [volonteers]
🌠 We get help
- Roscomsvoboda. Speech in Russian youtube.
- Privacy Accelerator
- Open Source World Community
- NixOS Community
🫂 Like-minded people
- Cloudron - commercial project, code closed, from $15 per month for email and multiple services. You have to install the application yourself on the server, keep an eye on the server resources.
- IndieWeb - it is open-source project, complicated in configuration.
- Kubenav - manages docker containers from mobile. Promising but for highly skilled users.
- Yunohsot - open-source project, but not very stable.
- FreedomBox - open source project on ARM
- Tunrkeylinux - ready to use software for advanced users
Useful
- https://ssd.eff.org
- https://datadetoxkit.org
- https://securityplanner.consumerreports.org/tool
- https://www.fordfoundation.org/work/our-grants/building-institutions-and-networks/cybersecurity-assessment-tool/
Politics
Our mission is humanitarian - to realize the right to privacy and confidentiality of anyone who wants it.
We are not involved in politics, we do not support or belong to political parties, we do not condemn anyone, and we do not participate in conflicts.
Privacy Policy
The mobile app is completely autonomous, it does not download any data from websites, does not contain any trackers, and interacts only with your server.
The server communicates with your NixOS infrastructure
The recommended client applications interact only with your server. Exceptions:
- Delta.Chat when using geolocation publishing forced use mapbox
- There are questions about bitwarden mobile app. It seems there are tracker libs, but the traffic has not analyzed yet, maybe not active.
Our web-resources
You leave a lot of your data when you visit any site. At a minimum, IP, at a maximum, all kinds of tracking data. We do not use tracking in any form, on any of our public services. But we aggregate access-logging to understand how many users we have and from what country. All visitor IPs are stored as subnets (x.x.x.0) and may not uniquely identify you. But we recommend to use means of traffic anonymization, as we do not guarantee that our server provider does not collect meta-information.
🤩 Opportunities
Most importantly, control your own digital life. Your communications, data, meta-information belong only to you!
To that end, we've implemented:
- Deployment of IT infrastructure without special knowledge from your mobile phone
- A lot of necessary and simply useful [services].
- Automatic backups
- Automatic updates
- Enabling and disabling services
- SSH access for advanced users
- 🗓️ Automatically add resources to the server: disk, memory, CPU
🧬 Project architecture
Yes, you could use kuburnetis. But why when immutability is ensured by NixOS?
Stack: NixOS, python, flutter
Mobile app
Flutter/Dart was chosen because of the speed and smoothness of the UI and cross-platform.
Backend
NixOS + Python. NixOS was chosen because of its reproducibility, python because of its versatility and popularity.
Service providers
We do not get paid by any service providers! We are not affiliated with them in any way. We chose them purely for professional reasons. But we do not exclude partnership in the future.
Hosting
Hetzer was chosen because of low price and acceptable level of service, quality REST API. Wasn't noticed any privacy or data collection issues.
Candidates:
- Own personal iron server. Our main priority right now.
- A service provider that will provide an API to deploy an iron server. Outside FVEY
- OVH
- Scaleway
- DigitalOcean
There's also free Oracle Cloud, but where you don't pay, you're usually a commodity.
DNS
Cloudlare reliable, free. Probably collects data, otherwise it's hard to explain why proxy other people's traffic for free. In our case we use it only as a DNS-server and do not proxy anything. In the future we will replace it with self-hosted DNS, as soon as we solve the reliability problem.
Backup repository
Backblaze is free or times cheaper than AWS. Not seen in data collection. Publishes in open source the hardware it runs on. And also shares very useful statistics about disk failures, on the basis of which you can choose the most reliable and tested one. In the future, perhaps, we will replace it with a self-hosted or p2p solution. Now it is not the main priority, because the data is encrypted, and the service provider sees only the ip of your server, but not the home one.
🔀 Roadmap
roadmap for project development
⚠️ Beta
The current release is not yet ready for everyday use by an unskilled user.
️ Project development vectors
in descending order of priority
🗓️ Plan
v0 (2020) 🏁
- Server deployment from mobile phone
- Automatic backup
- Automatic update
- Turn on and off services
- SSH access for power users
v1 (2021)
- <contributor support system
- Automatic unmounting from backup
- Automatic disk expansion
- Automatic memory addition
- Disk encryption
- Automatic rollback of failed updates
- Biometric authentication
- Launch on Apple Store and Google Play
- <can delete gmail
- <collaborative services DNS-slave, p2p backup>
- <support system
v2 (2021-2022)
- Request-driven service installation
- Support not only cloud server but also hardware (presumably Rpi4)
- Management of multiple servers from a single mobile app
- Service UI generation on the backend (json)
- UI/UX refactoring
- De-bug-logging to help the users without private data disclosure
-
. - <possible in the Enterprise
v3 (fancy)
- cluster (microhosting)
- Private smartphone (PinePhone)
- Private Desktop
🔒 Privacy
_Accessibility to information by a third party. That's our top priority!
- Server is rented by you, belongs only to you
- No telemetry, cookies, logs, licenses, moderation, user agreements, tracking etc.
- All connections to the server are securely encrypted
- VPN
🗓️ How else will we increase privacy?
- Encrypting data on the server
- Installing SelfPrivacy Server on an iron PC (intel nuc / rpi4)
- DNS-resolver
- Private Server-to-Server Interoperability Transport (yaggdrasil)
- Backup to Decentralized Storage (Tahoe-LAFS or NextCloud p2p)
⚠️ Restrictions
The virtual server is not exclusively private. The service provider technically has access to the memory and disk of your server. A virtual server is much more private than a centralized public service!
🗓️ We are working on making SelfPrivacy Server possible to install on your server at home
🛡️ Safety
No chance for an intruder to break into your system
- BugBounty (after v1)
- Regular vulnerability scanning
- Only use open source code
How else do we improve security?
- hardware token (Nitrokey)
- tang/clavis?
- auto-updates with automatic rollback
- kernel hardering
Autonomy
Strategy - digital independence
In the early days of the Internet, it was decentralized. The system administrator had to take care of everything. Nowadays, not much has changed, and whoever wants a private IT infrastructure has to build it himself in almost the same way as 20 years ago, or use non-private cloud services.
We've stepped back, sideways and forward. We have developed a tool that automatically creates your own private IT-infrastructure without involving a system administrator. Using such an infrastructure is almost as easy as using cloud services. At least, that is what we strive for.
SelfPrivacy App/Server may not need to be upgraded, it will still work. But then you will lose patches, possibly critical ones, and new handy features. You can keep an eye on our repository or look at roadmap.md for changes.
🤗 User friendliness
We do our best to make our service convenient for common users:
- Automate complex operations of hosting providers, server and services management
- Taking care of data encryption and backups
- Add reliable and secure [services.md]
- Work with professional UI/UX designer
- Support 8x5 users (during working hours): on public telegram channel (en/ru)
🗓️ Plans
- Improved documentation
- Screencasts with detailed explanation
- Streams, public meetings
- Maybe a forum, a ticketing page
Anonymity
Hiding the author of the message. This is not our main priority. We ensure privacy first and foremost.
Marketing
Unfortunately, even open source needs marketing. In the sense that we have to somehow make users aware of the possibilities for solving their privacy problems.
User sources
Media plan
- Channel in Fediverse
- App stores
- Post information from services
- Habr
- Software comparison services
- Lower telegram channels
- News open source (opennet)
- Aggregators (github awesome)
- Youtube?
- SelfPrivacy video
We have already been helped by
DevOps Release Management
Lending
Pipeline
commit -> push -> webhook -> checks -> selfprivacy.org
ToDo
- Do I need translation?
- Check for broken links
- Spellchecker
Docs
Pipeline
commit -> push -> webhook -> checks -> mdbook -> translate -> docs.selfprivacy.org
ToDo
- translate
App
Mobile App
Pipeline
Checklist
ToDo
Server
Pipeline
Checklist
ToDo
Preset
Accounts with service providers are required to use SelfPrivacy
Installation
_prepared instruction
🧰 Services
SelfPrivacy functionality grows through services:
- communication
- personal privacy and digital independence services
- development tools
| service | status | central user management | isolation | backup |
|---|---|---|---|---|
| 🏁 | ✅ | ✅ | ||
| Pleroma | 🏁 | ❌ | ✅ | ✅ |
| [NextCloud] (cloud.md) | 🏁 | ❌ | ✅ | ✅ |
| [Bitwaden] (pass.md) | 🏁 | ❌ | ✅ | ✅ |
| Gitea | 🏁 | ❌ | ✅ | ✅ |
| OpenConnect | ⚒ | ✅ | ✅ | ✅ |
| SearX | 🗓️ | - | - | - |
| XMPP | 🗓️ | - | - - | |
| syncserver FF | 🗓️ | - | - - | |
| Jitsy | 1F5D3↩️ | - | - - | |
| OwnCast | 🗓️ | - | - - | |
| PeerTube | 🗓️ | - | - - | |
| Matrix | 1F5D3↩️ | - | - - | |
| Mumble | 1F5D3↩️ | - | - | |
| Geo Serivce | 🗓️ | - | - - | |
| Web site | 1F5D3↩️ | - | - - | |
| Dev services | 🗓️ | - | - - | |
| ID/DID | 🗓️ | - | - - |
🗓️ Plans
Add themed software selections:
- Gaming
- Private Data processing
- Enterprise software
Rechargeable sources
- https://github.com/awesome-selfhosted/awesome-selfhosted
- https://search.nixos.org/packages
Important for registering with services, receiving notifications, and as a server for Delta.Chat. Tutanota and Protonmail do not support third-party email clients and Delta.Chat (no IMAP).
Typical data leaks when using third-party servers
- IP once per minute. Helps determine your location: at home, away from home, at work.
- Contents of your messages: what services you are registered on, bank and medical statements and more.
- Meta-information: with whom and when you communicate, even if you use encryption.
Alias to addresses.
Messages for user+alias@domain.com will come to user@domain.com.
Filter directories
The message for user-dir@domain.com will create a dir directory in the user@domain.com mailbox. All mail for user-dir@domain.com will arrive in the dir directory.
Web interface
It may seem undeveloped or outdated to some. But it has the advantage of simplicity and small amount of code and bugs, which increases [security.md] and [privacy.md]. But it is better to use email clients and disable the web interface in SelfPrivacy App. This will reduce the attack surface and the risks of hacking.
Recommended email clients
- Mozilla Thunderbird
- FairEmail (Android)
- ? (iOS)
- ? (PinePhone)
Tips
- Email over 50 years old. In IT, it's a sign of technology maturity and reliability.
- Email, the most popular way to get infected with viruses, after installing them yourself with unlicensed software and cracks.
- Beware of phishing, it can rob you of your savings and control over your digital life.
- Create filter directories for different purposes. This will help protect against phishing and cluttering your inbox. Examples:
user-w@domain.com- for registering with web services- User-shops` - for web-stores
user-pay- payment systems- User-forum` - forum notifications
- Use aliases for questionable services or one-time needs, such as
user+tmp@domain.com. By aliases convenient to filter and mass delete mails. It is also convenient to find out exactly where your mail was leaked from.
Messenger
Messengers like Telegram, Signal, Whatsapp can't be private due to the peculiarities of architecture - centralization. And peer-to-peer (p2p) services like tox consume too many resources and are inconvenient to use on a mobile device. The best solution is to use our own server.
- Delta.Chat - uses your personal email server
- Matrix - promising development, will be added to SelfPrivacy after stabilization.
- XMPP/IRC - great candidates, will probably be added to SelfPrivacy later.
- Rocket.Chat, Zulip, Mattermosht - no convenient way to communicate between servers.
Typical data leaks when using alien servers
- IP once per minute. Helps determine your location: at home, away from home, at work.
- The content of your messages.
- Meta-information: with whom and when you communicated, even if you use encryption.
Features of Delta.Chat
- Regular email client with all the features of IM.
- Reliable end-to-end encryption (e2e), provided a personal email server is used by both interlocutors or a personal key exchange, such as via QR code.
- Can use any email server, but then you lose control over the meta-information and risk key-swapping man-in-the-middle attack.
- Slightly slower than usual messengers
- First message is not encrypted because public encryption keys are sent with it.
- There are problems with sending files > 5-7MB.
- There are no convenient channels. We recommend using decentralized social network
Decentralized social network
Substitute: twitter Alternative: mastodon, frendica
Any centralized social network will have to take care of moderation, censorship, implementation of rules, reading your correspondence as it grows. Another thing is your own social network, which can only belong to you, your family or your team. Only a decentralized network can provide maximum privacy. That's why we offer you to become part of the decentralized network Fediverse. At SelfPrivacy we use Pleroma.
Typical data leaks when using other people's servers
- IP once per minute. Helps determine your location: at home, away from home, at work.
- The content of your messages.
- Meta-information: with whom and when communicated.
Features of Pleroma.
- Social network of any scale: from personal server with only one account to thematic.
- Your social network, your rules. You are censor, moderator and administrator.
How to use
How to administer
Code repository - gitea
File cloud
nextcloud
VPN - openConnect
Password manager - bitwarden
🚀 Donations
Unfortunately, you can't make a mass product on enthusiasm. Many choose to go the commercial route, but that imposes limitations:
- A focus on making money, not privacy
- Willingness to sell out to a mega-corporation
- Functionality dictated by market, marketing, buzzwords.
I'm struggling to find another way. The best of which is direct regular user funding. At least $1 a month.
As of 2019, I'm investing a noticeable chunk of my family budget and time into the project. Because I am confident in the necessity of SelfPrivacy. Kirill Zholnay (founder).
Monero cryptocurrency wallet
83sxCzpY9Be2a7CCkrML6JamwLoQ6C7h6h9E282LqNJjZC7Gx2aVcNR9Kz8Mqrix8s7zXyUpWgtVYQByraqqopx38Y4xDGQ
For regular money Librepay
https://liberapay.com/SelfPrivacy.org/
Volunteering
If you use SelfPrivacy - you're already helping by creating an independent internet. Tell your friends, give them an account on your server and independence will become a little more important.
If you want to help SelfPrivacy startup directly:
- Support financially on a regular basis. Even $1 a month, but regularly will help us a lot. Then we see that our efforts are not in vain and our project is important to someone.
- Get edits, translations, bug-fixes, or new functionality into our repository: https://git.selfprivacy.org
- Give advice, report a bug, or just say a few nice words: hello@selfprivacy.org
Foundations
https://nlnet.nl/foundation/ want support )
Developers
How to help the project:
- Correct the documentation
- Translate the documentation (most likely automated by machine translation)
- Complete or fix the backend
- Help with flutter on mobile app
- UX/UI design (figma)
DevOps Release Management
Lending
Pipeline
commit -> push -> webhook -> checks -> selfprivacy.org
ToDo
- Do I need translation?
- Check for broken links
- Spellchecker
Docs
Pipeline
commit -> push -> webhook -> checks -> mdbook -> translate -> docs.selfprivacy.org
ToDo
- translate
App
Mobile App
Pipeline
Checklist
ToDo
Server
Pipeline
Checklist
ToDo
SelfPrivacy Project Contribution Guide
Contents
- Getting Started
- Intended Audience
- Requirements
- Working with
git- Registering on our Gitea instance
- Forking
- Cloning
- Editing
- Comitting changes
- Reviewing
- Making a pull request
- Contributing
- SelfPrivacy webpage
- Getting the repository
- Repository structure
- Application translations
- Getting the repository
- Repository structure
- SelfPrivacy webpage
Getting Started
Welcome to the SelfPrivacy Project Contribution guide. This document is brought to you by SelfPrivacy team to help people willing to contribute into our project. This document contains quick explanation of everything you'll need to help the project growing, developing and improving.
Intended Audience
This document is divided into two parts and depending on your experience of working with a technical projects, you may be interested in reading both or just one of the parts.
If you have a basic understanding of git version control system and had previous experience of working with Gitea git server, then you'll probably be interested in skipping the first part as it contains the most basic concepts of git explained and illustrated using Gitea as an example.
In case if all(or some) of the mentioned things is relatively new to you - feel free to look into first part. It covers the minimal amount of the things that you'll need to get started.
Requirements
- Basic command shell(CLI) skills
- Git concepts understanding
Working with git
What git is
Git - is one of the most popular version control systems, used by millions of developers and libre/open source contributors all over the world.
This is very powerful tool that provides your files(mostly, your code) with change tracking, fault tolerance, versioning and work separation for teams and different environments. Such power is provided at a cost of implementing a couple of new concepts that needed to be understood before starting to work with git. Those concepts are not complicated so it's not a big challenge to understand them.
To tell long story short, git expects code to be stored on the remote server in the repository. You work with code by downloading(cloning) repository to your computer. When you make changes to your local copy of a repository, you give git a command to syncronize changes in your local copy of repository with remote one. When you syncronize your changes, git server(Gitea in our case) records each change you've done. If something goes wrong with your code, you can rollback to it previous version.
A few words about Gitea
As far as I mentioned, git expects you to store your code in the remote repository. For this reason the remote server required to store your code. You might have already heard about a couple. The most popular include:
- Github
- Gitlab
- Bitbucket
The problem of this services is that they are owned by big corporations like Microsoft or Atlassian, so it means that when they offer to hold your code for no cost, they use access to your private data as a fee for using their development in which they invest millions of dollars(it fully pays off itself, in fact).
As we are the project that fights to allow people to defend their privacy, we can't trust our code to those information-devouring companies. For this reason we chosen a git server that can be hosted on a self-hosted private server that server our developments for the sake of community. For us this server is Gitea. It can be accessed here.
Except repositories and cloning, concepts of git, you'll need to be
acknowledged with are: commit and push.
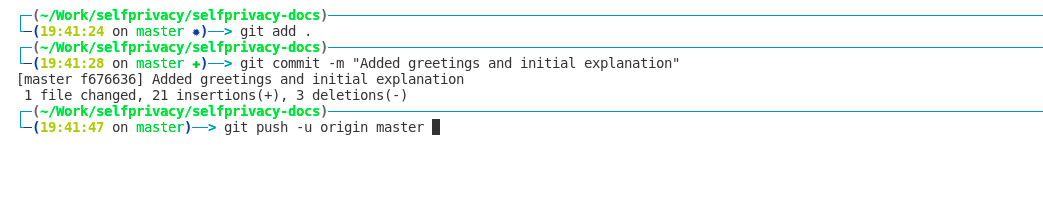
Author commits changes to this article :)
Not to bore you completely with the theory, let's jump to the part where all of the fun begins,
Registering on our Gitea instance
-
First of all, go to the link, where our Gitea can be found: https://git.selfprivacy.org
-
You will be presented with the following picture:
You will need an upper right corner of this webpage:
-
Push a
Registerbutton -
You will be presented with quite standard registration form:
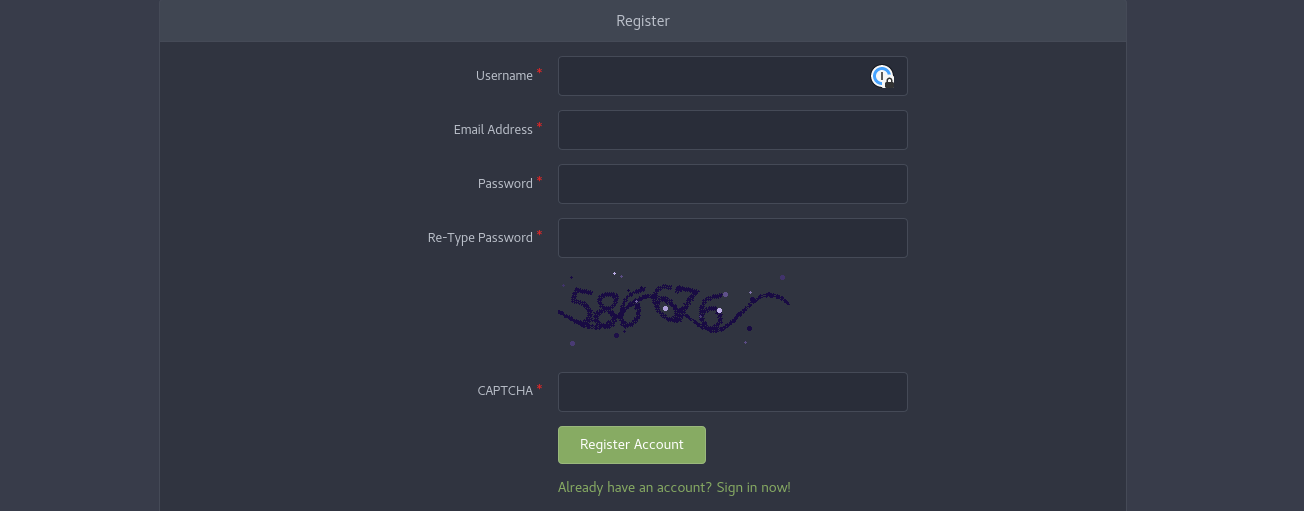
-
Complete the registration. Do not forget to create a strong and memorable password.
-
After completing the registration, log into the Gitea.
My congratulations. You have successfully registered an account on Gitea
Forking
Remember, I mentioned a couple of new concepts that git introduces, right? Forking - is one of them. But before I explain what does it mean, let me briefly explain how to access existing repositories.
- After successful registration and login you'll be presented with your repositories list, commit activity heatmap and a repository search:
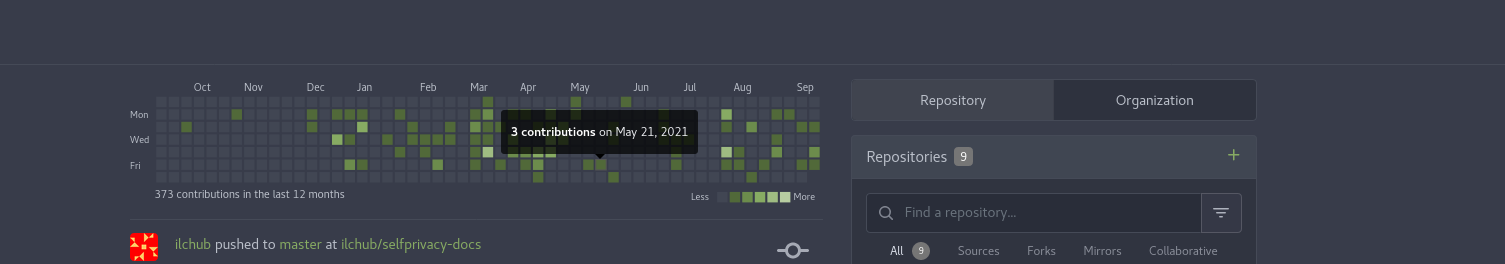
- Please use a search bar to search for repository that you want to contribute:
- When you search for the repository, found ones will appear as a search result. Click on the one, you want to contribute to.
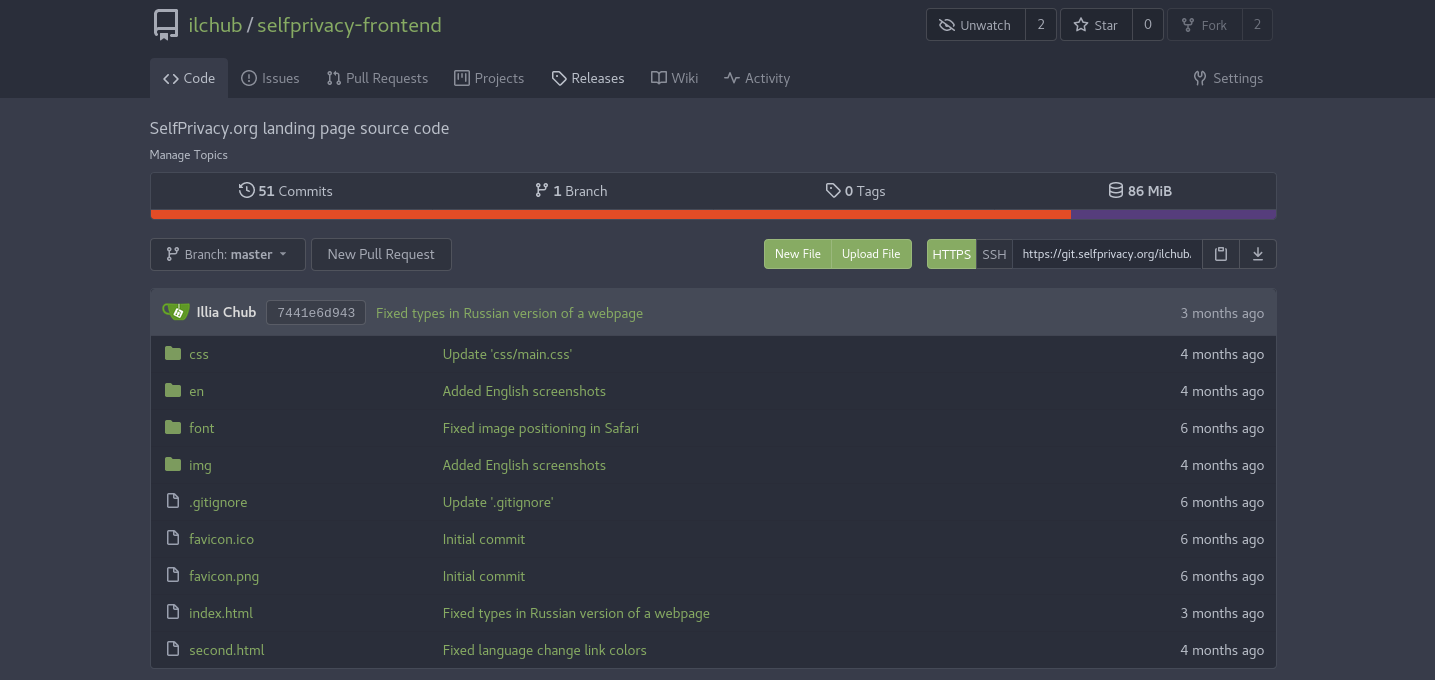
SelfPrivacy webpage repository page
Now, let's go back to forking. When you want to make some changes to the sources in the repository, you can't commit changes to the original one directly, unless you're granted permission to. Usually, the only people that have permission to directly modify the repository, are the core development team. For all the contributors there's different apprach exist.
Contributors can modify the original repository by creating an identical copy of it on their own account, making changes to it and requesting moderators to overwrite(or merge) files with changed ones. Moderator reviews changes before approving them, gives some comments regarding the changes and if everything is OK, then he/she accepts proposed changes.
Forking - Creating an identical copy of a repository on your own account of a git server
To fork a git repository, you'll have to push a Fork button(can be found at the upper right corner of the repository interface):
When you'll fork the repository, the identical one will appear in your account and you'll be able to make modifications to it.
Cloning
Remember, I said that wheen you're working with a code inside of a git repository, to make some changes, you'll firstly have to clone it to your computer, right?
Now it's time for me to show you how to begin making changes to your code.
To clone a repository, you'll have to use a CLI git utility. let's begin with opening your terminal:
Microsoft Windows users would have to open a "PowerShell" application. Mac users will be able to find a "Terminal" app in the "Utilities" folder.
First of all, you'll have to pick a location where you would like to store the repository with a code. It can be specially created, deticated folder, or just your home directory
For our example let's pick home directory as the folder to which we'll clone our repository(home folder opened by default by the most shells).
Let's clone a webpage repository to our computer. To do so, please run the following command:
git clone https://git.selfprivacy.org/ilchub/selfprivacy-frontend
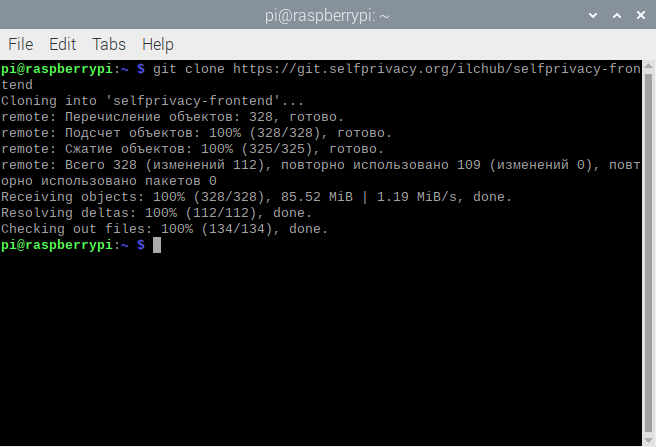
If you'll now open the file manager, you'll see the newly cloned repository(which is now just a folder on our disk :)
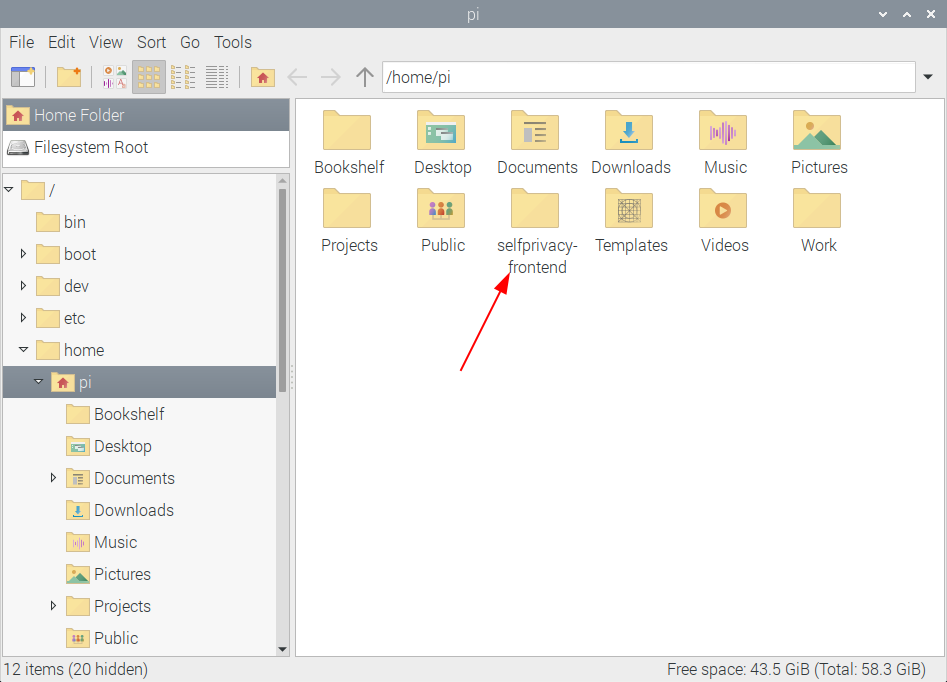
From this point we can start editing project files
Editing
Editing of a project is a subject of quite personal taste. From the point of getting the code to your computer, it's totally up to you, what code editor to choose. Author used (Neo)Vim and VS Code to write the following article.
Author, writing article in the VS Code
Feel free to explore the repository and edit it in a way you want.
Commiting
After you've made all desired changes, time comes to push your changes to the Gitea server to store them in a safe place and keep track of them. In the world of git, making changes to the source code is described by pretty self-explainable word - commiting. To commit changes to the code, we'll again need to use some CLI skills.
Open your terminal and make sure that you're currently in the same directory that code resides in. Your current directory can be determined by running the following command:
pwd
and it defaults to your home folder:
In case if you're not in the same directory with your code, you can change by running the following command:
cd /path/to/the/directory/with/my/code
After that you can again rerun pwd to make sure that directory is correct.
When the requirement of being in the correct directory is met, you can start commiting your changes.
First of all, please run the following command:
git add .
This command will result in git searching recursively through the entire directory for changes you've made in the files:
This command will produce no output so don't be worried by that fact.
After searching for changes, your next step will be to add them to the queue for syncronization with the Gitea server. To do so, please run the following:
git commit -m "Brief explanation of changes"
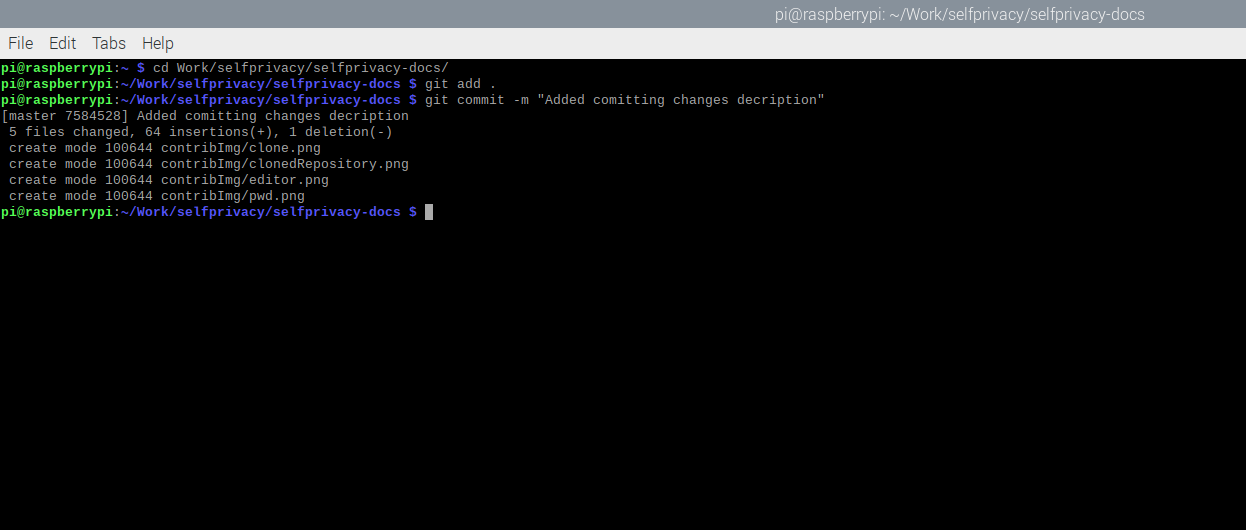
This command will output all changes that were made to the folder(of course in case if you defined a correct search scope with git add command).
That's the point when all your changes are indexed and queued for being pushed to the remote server. To push changes to the remote server, please run:
git push -u origin master
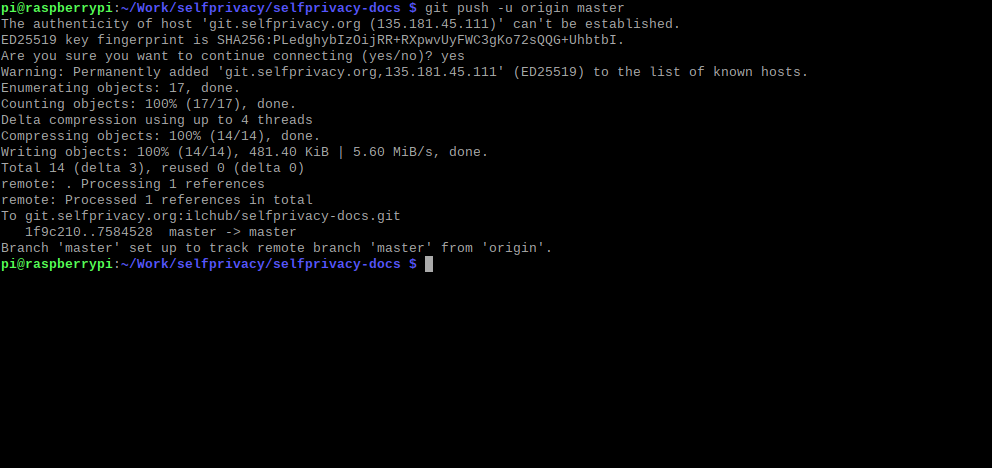
My congratulations. Your changes have been successfully written ton the remote repository. You can wisit Gitea to check them. You should now see your fresh changes.
Reviewing
Right after pushing your changes to the remote repository, it's rather good idea to review them. If you'll visit your repository, you'll see that the last commit on the page have changed:
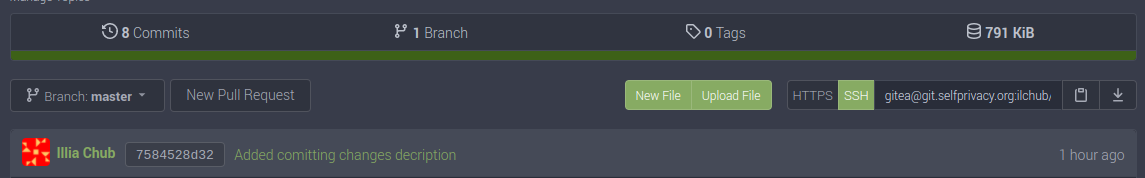
You can click the "Commits" button to see the history of all your commits:
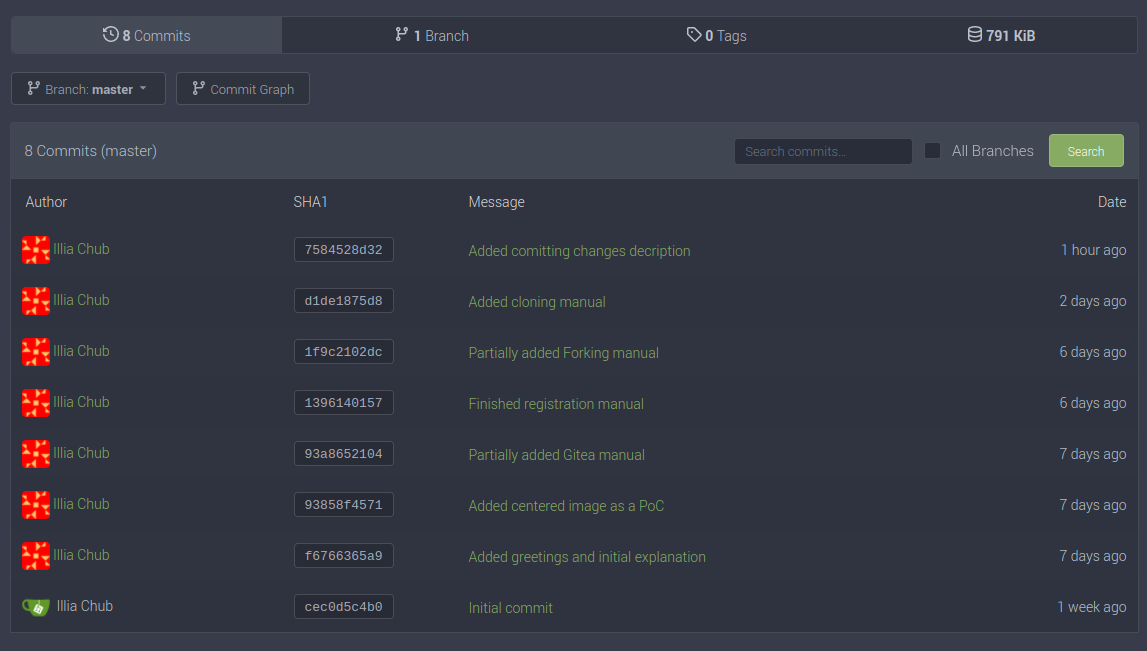
If you'll click onto one of the commits, you will be able to see what things changed since last push:
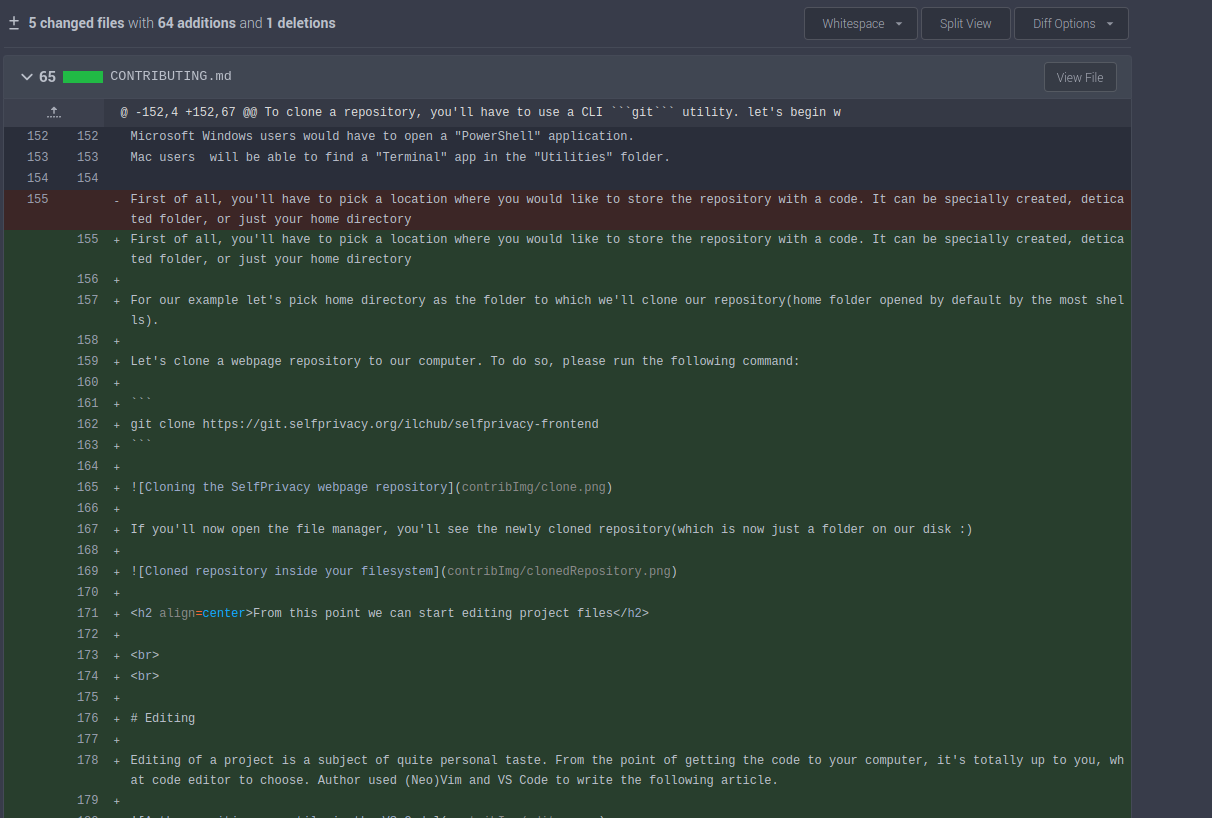
Gitea will show you the detailed explanation on what have been added to your code and what have been removed.
That's how changes review works.
Note: You can add comments to each line by clicking on it.
Contributing
SelfPrivacy Webpage
Repository URL
https://git.selfprivacy.org/ilchub/selfprivacy-frontend
Application translations
Repository URL
https://git.selfprivacy.org/kherel/selfprivacy.org.app
How we test
waiting nikolai